
win7x64虚拟机(过NPTPVMPSEGKG盾无限替换vmx)是一款VMP过虚拟机检测系统,早期时候做了一个过G盾的,重新做个新的吧.花了一晚上时间做出,虚拟机过NPTPVMPSEGKG盾。压缩的时候忘记随机mac了,大家换个吧,这个大体不影响。
系统说明
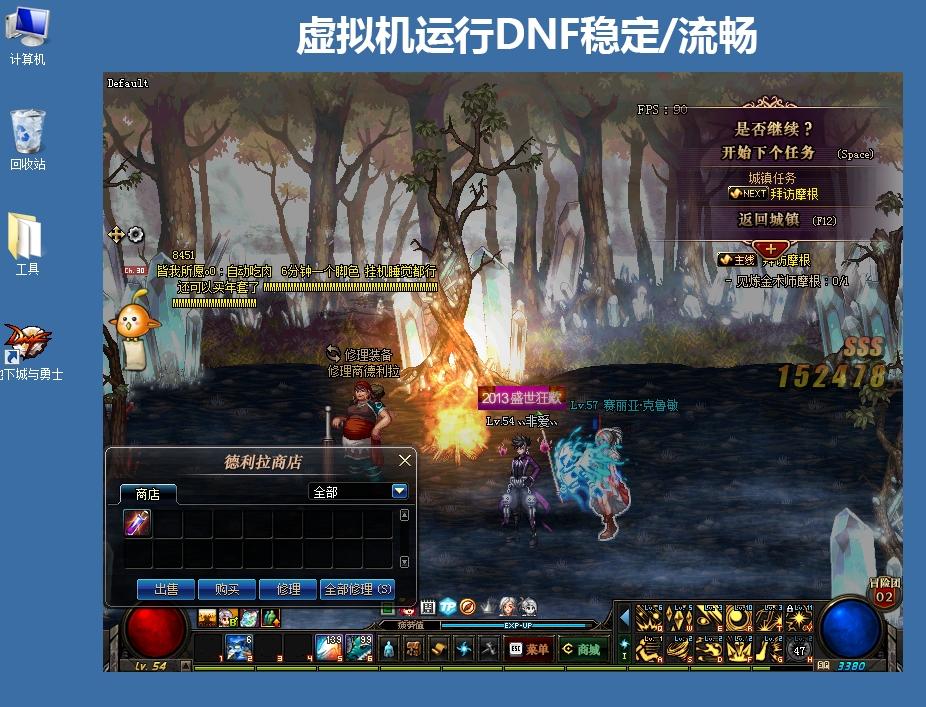
可以玩DNFCF一些游戏
提取码:ah3f
关于Win7x64下过TP保护
调试对象:DXF调试工具:OD、Windbg调试环境:Win7SP1X64
内核层部分:x64下因为有PatchGuard的限制,很多保护都被巨硬给抹掉了。比如SSDTHookInlineHook所以TP无法继续使用这些保护手段了。除非腾Xun冒着被巨硬吊销数字签名的风险来阻止我们调试。我曾经在看雪论坛里看过有个人写的文章,它亲自测试在x64环境下清零调试端口,结果发生了蓝屏,所以在x64下TP是不会清零的。这样就省了不少的事情。但是自从那次TP大更新后新加入了ValidAccessMask清零。那么在ring0中TP除了ValidAccessMask清零,还有反双机调试,这里不是我们讨论的范畴。我们只是讨论如何才能正常调试游戏,于是在内核层我们只要解决ValidAccessMask清零就可以了。调试权限(ValidAccessMask)的清零这个标志位其实是DebugObject(调试对象)的权限,如果为0将导致无法创建调试对象(缺少权限)。常见的情况就是OD无法附加任何进程,这个保护刚刚出的时候很多菜鸟都没搞懂,包括我自己(知道被我师傅说我等级太低时的心情是什么?。这个DebugObject在很多调试函数中都有用到,比如NtCreateDebugObject就有需要访问调试对象。所以要想办法恢复这个标志位。我们有三种选择:1、自己恢复原来的值2、找到TP清零的位置Nop掉3、移位(重建DebugObject)这里我选择了第一种。具体步骤如下:①定位DebugObject:在NtCreateDebugObject里就有DebugObject的地址。1:kdufNtCreateDebugObjectnt!NtCreateDebugObject:fffff800`042697a048895c2408????mov????qwordptr[rsp+8],rbxfffff800`042697a54889742410????mov????qwordptr[rsp+10h],rsifffff800`042697aa57??????????push??rdifffff800`042697ab4883ec70??????sub????rsp,70hfffff800`042697af418bf9??????mov????edi,r9dfffff800`042697b28bf2????????mov????esi,edxfffff800`042697b4488bd9??????mov????rbx,rcxfffff800`042697b765488b042588010000mov??rax,qwordptrgs:[188h]fffff800`042697c0448a90f6010000??mov????r10b,byteptr[rax+1F6h]fffff800`042697c74584d2??????test??r10b,r10bfffff800`042697ca7414????????je????nt!NtCreateDebugObject+0x40(fffff800`042697e0)nt!NtCreateDebugObject+0x2c:fffff800`042697cc488b052d38e5ff??mov????rax,qwordptr[nt!MmUserProbeAddress(fffff800`040bd000)]fffff800`042697d3483bc8??????cmp????rcx,raxfffff800`042697d6480f43c8??????cmovae??rcx,raxfffff800`042697da488b01??????mov????rax,qwordptr[rcx]fffff800`042697dd488901??????mov????qwordptr[rcx],raxnt!NtCreateDebugObject+0x40:fffff800`042697e048832300??????and????qwordptr[rbx],0fffff800`042697e441f7c1feffffff??test??r9d,0FFFFFFFEhfffff800`042697eb740a????????je????nt!NtCreateDebugObject+0x57(fffff800`042697f7)nt!NtCreateDebugObject+0x4d:fffff800`042697edb80d0000c0????mov????eax,0C000000Dhfffff800`042697f2e9e4000000????jmp????nt!NtCreateDebugObject+0x13b(fffff800`042698db)nt!NtCreateDebugObject+0x57:fffff800`042697f7488d442450????lea????rax,[rsp+50h]fffff800`042697fc4889442440????mov????qwordptr[rsp+40h],raxfffff800`042698018364243800????and????dwordptr[rsp+38h],0fffff800`042698068364243000????and????dwordptr[rsp+30h],0fffff800`0426980bc744242868000000mov????dwordptr[rsp+28h],68hfffff800`04269813488364242000??and????qwordptr[rsp+20h],0fffff800`04269819458aca??????mov????r9b,r10bfffff800`0426981c488b158dd3daff??mov????rdx,qwordptr[nt!DbgkDebugObjectType(fffff800`04016bb0)]fffff800`04269823418aca??????mov????cl,r10bfffff800`04269826e84572f1ff????call??nt!ObCreateObject(fffff800`04180a70)fffff800`0426982b4c8b4c2450????mov????r9,qwordptr[rsp+50h]fffff800`042698304c894c2460????mov????qwordptr[rsp+60h],r9fffff800`0426983585c0????????test??eax,eaxfffff800`042698370f889e000000??js????nt!NtCreateDebugObject+0x13b(fffff800`042698db)这个红字就是了继续定位ValidAccessMask的地址。1:kddqfffff800`04016bb0fffff800`04016bb0??fffffa80`00c3320000000000`00000000fffff800`04016bc0??fffff8a0`0009a0100000002a`00000012fffff800`04016bd0??00000024`000000a1fffff880`0119d9a0fffff800`04016be0??00000002`00000001fffff880`095deaccfffff800`04016bf0??fffff800`03f873f000000000`00000007fffff800`04016c00??00000003`00000000fffff800`03e10448fffff800`04016c10??fffffa80`01bae06000000000`00000000fffff800`04016c20??00000000`0000000000000003`000001011:kddt_OBJECT_TYPEfffffa80`00c33200nt!_OBJECT_TYPE+0x000TypeList??????:_LIST_ENTRY[0xfffffa80`00c33200-0xfffffa80`00c33200]+0x010Name????????:_UNICODE_STRING"DebugObject"+0x020DefaultObject??:(null)+0x028Index????????:0xb''+0x02cTotalNumberOfObjects:0+0x030TotalNumberOfHandles:0+0x034HighWaterNumberOfObjects:0+0x038HighWaterNumberOfHandles:0+0x040TypeInfo??????:_OBJECT_TYPE_INITIALIZER+0x0b0TypeLock??????:_EX_PUSH_LOCK+0x0b8Key??????????:0x75626544+0x0c0CallbackList????:_LIST_ENTRY[0xfffffa80`00c332c0-0xfffffa80`00c332c0]1:kddt_OBJECT_TYPE_INITIALIZER?fffffa80`00c33200+40nt!_OBJECT_TYPE_INITIALIZER+0x000Length????????:0x70+0x002ObjectTypeFlags??:0x8''+0x002CaseInsensitive??:0y0+0x002UnnamedObjectsOnly:0y0+0x002UseDefaultObject:0y0+0x002SecurityRequired:0y1+0x002MaintainHandleCount:0y0+0x002MaintainTypeList:0y0+0x002SupportsObjectCallbacks:0y0+0x002CacheAligned????:0y0+0x004ObjectTypeCode??:0+0x008InvalidAttributes:0+0x00cGenericMapping??:_GENERIC_MAPPING+0x01cValidAccessMask??:0x1f000f+0x020RetainAccess????:0+0x024PoolType??????:0(NonPagedPool)+0x028DefaultPagedPoolCharge:0+0x02cDefaultNonPagedPoolCharge:0x58+0x030DumpProcedure??:(null)+0x038OpenProcedure??:(null)+0x040CloseProcedure??:0xfffff800`042b18e0????void??nt!DbgkpCloseObject+0+0x048DeleteProcedure??:0xfffff800`04105200????void??nt!xHalEndOfBoot+0+0x050ParseProcedure??:(null)+0x058SecurityProcedure:0xfffff800`04170530????long??nt!SeDefaultObjectMethod+0+0x060QueryNameProcedure:(null)+0x068OkayToCloseProcedure:(null)于是我们就定位到了VaildAccessMask的地址了。②恢复工作它的默认值是0x1F000F当我们自己手动修改成0时。使用OD附加任意进程。
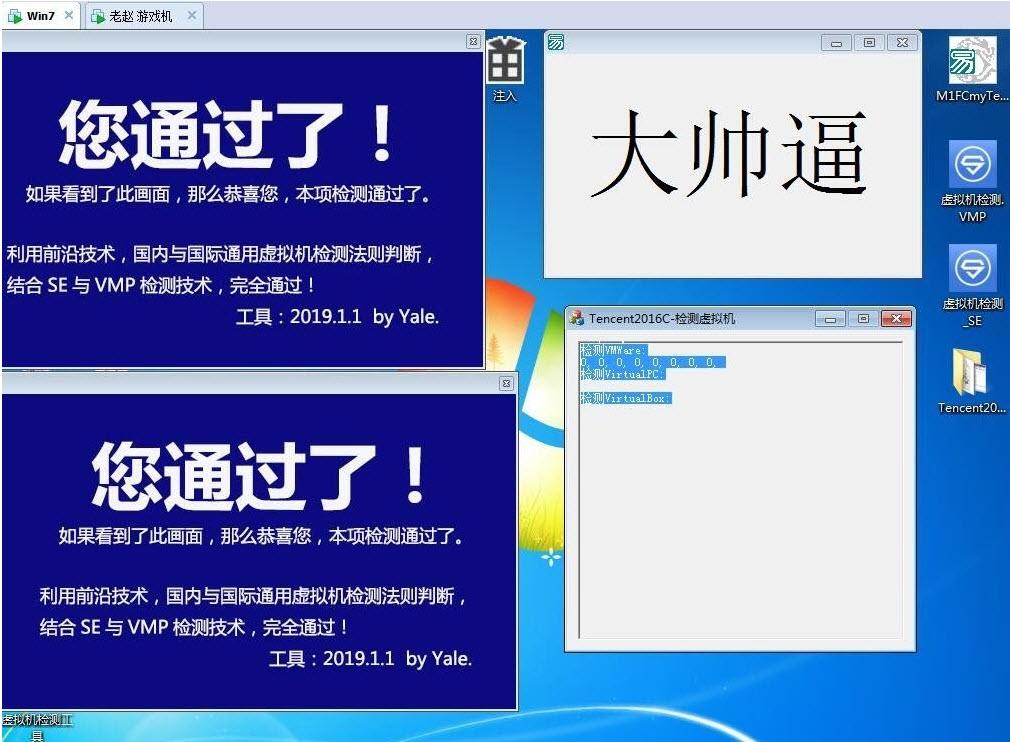
Tags:x64dbg使用,永久激活,虚拟机系统.
 驱动精灵去广告版+单文件版+万能网卡驱动包硬件驱动 / 244.75MB / 2015-10-15 / WinAll / /
驱动精灵去广告版+单文件版+万能网卡驱动包硬件驱动 / 244.75MB / 2015-10-15 / WinAll / / 小编点评:驱动精灵去广告版+单文件版+万能网卡驱.
下载 星谷CP-630K打印机驱动硬件驱动 / 748.84MB / 2019-9-8 / WinAll, WinXP, Win7 / /
星谷CP-630K打印机驱动硬件驱动 / 748.84MB / 2019-9-8 / WinAll, WinXP, Win7 / / 小编点评:星谷CP-630K打印机驱动是一款官.
下载 雷柏VH600耳机驱动硬件驱动 / 80.45MB / 2021-10-29 / WinAll / / 深圳雷柏科技股份有限公司 /
雷柏VH600耳机驱动硬件驱动 / 80.45MB / 2021-10-29 / WinAll / / 深圳雷柏科技股份有限公司 / 小编点评:雷柏VH600耳机驱动是由深圳雷柏科技.
下载 双人暗夜精灵战役1.0.2游戏地图 / 569.61MB / 2015-2-26 / WinAll, WinXP, Win7, win8 / /
双人暗夜精灵战役1.0.2游戏地图 / 569.61MB / 2015-2-26 / WinAll, WinXP, Win7, win8 / / 小编点评:双人暗夜精灵战役1.0.2【攻略】.
下载 拿破仑:全面战争汉化补丁汉化补丁 / 175.63MB / 2023-10-24 / WinXP / /
拿破仑:全面战争汉化补丁汉化补丁 / 175.63MB / 2023-10-24 / WinXP / / 小编点评:拿破仑:全面战争是著名即时战略游戏全面战争系列.
下载 吸血鬼莱恩:背叛汉化补丁汉化补丁 / 618.99MB / 2021-7-12 / WinAll, WinXP, Win7 / /
吸血鬼莱恩:背叛汉化补丁汉化补丁 / 618.99MB / 2021-7-12 / WinAll, WinXP, Win7 / / 小编点评:吸血鬼莱恩:背叛汉化补丁是业内知名的.
下载 纪元2205汉化补丁汉化补丁 / 250.20MB / 2012-4-11 / WinAll, WinXP, Win7 / /
纪元2205汉化补丁汉化补丁 / 250.20MB / 2012-4-11 / WinAll, WinXP, Win7 / / 小编点评:纪元2205汉化补丁是同名游戏的中.
下载 泰拉瑞亚Terraria正版B1.3.2.1完整汉化补丁汉化补丁 / 671.10MB / 2010-12-18 / WinAll, WinXP, Win7, win8 / /
泰拉瑞亚Terraria正版B1.3.2.1完整汉化补丁汉化补丁 / 671.10MB / 2010-12-18 / WinAll, WinXP, Win7, win8 / / 小编点评:泰拉瑞亚Terraria正版B1.3.2.
下载 职业玩家经理轩辕汉化组完整汉化补丁汉化补丁 / 144.1MB / 2018-8-9 / WinXP, Win7, win8 / /
职业玩家经理轩辕汉化组完整汉化补丁汉化补丁 / 144.1MB / 2018-8-9 / WinXP, Win7, win8 / / 小编点评:职业玩家经理是一款非常不错的模拟类游.
下载 缺氧Oxygen Not Included轩辕汉化补丁汉化补丁 / 209.73MB / 2023-6-3 / WinXP, Win7, win8 / /
缺氧Oxygen Not Included轩辕汉化补丁汉化补丁 / 209.73MB / 2023-6-3 / WinXP, Win7, win8 / / 小编点评:?《缺氧OxygenNotIncluded》.
下载 善良的死神新编V1.95正式版游戏地图 / 450.3MB / 2013-7-29 / WinXP, WinAll / /
善良的死神新编V1.95正式版游戏地图 / 450.3MB / 2013-7-29 / WinXP, WinAll / / 小编点评:善良的死神新编V1.9正式版隐藏英雄--.
下载 神之墓地2.6A游戏地图 / 412.22MB / 2021-6-1 / WinXP, win7 / /
神之墓地2.6A游戏地图 / 412.22MB / 2021-6-1 / WinXP, win7 / / 小编点评:请在魔兽1.24下运行该版本更新简介.
下载 神界危机2012冰封游戏地图 / 540.92MB / 2021-3-30 / WinXP, WinAll / /
神界危机2012冰封游戏地图 / 540.92MB / 2021-3-30 / WinXP, WinAll / / 小编点评:神界危机2012第三版【冰封】难度相.
下载 绝境幸存者无限金币版下载-绝境幸存者破解版下载v1.1 安卓最新版
绝境幸存者无限金币版下载-绝境幸存者破解版下载v1.1 安卓最新版 西部枪手破解版下载-西部枪手中文破解版下载v1.7 安卓版
西部枪手破解版下载-西部枪手中文破解版下载v1.7 安卓版 点亮星空手游九游版下载-点亮星空九游版下载v3.0.1 安卓版
点亮星空手游九游版下载-点亮星空九游版下载v3.0.1 安卓版 像素恶棍大吃鸡游戏下载-像素恶棍大吃鸡汉化版下载v1.0 安卓版
像素恶棍大吃鸡游戏下载-像素恶棍大吃鸡汉化版下载v1.0 安卓版 命令打击手机版下载安装-命令打击游戏(Command Strike)下载v1.2.4 安卓版
命令打击手机版下载安装-命令打击游戏(Command Strike)下载v1.2.4 安卓版 菁英特工游戏下载-tom clancys菁英特工下载v1.0.2 安卓最新版
菁英特工游戏下载-tom clancys菁英特工下载v1.0.2 安卓最新版 梦幻飞仙红包版下载-梦幻飞仙红包版官方版下载v9.2 安卓版
梦幻飞仙红包版下载-梦幻飞仙红包版官方版下载v9.2 安卓版 华为手机孤岛先锋下载-孤岛先锋华为版下载v1.400052.496077 安卓版
华为手机孤岛先锋下载-孤岛先锋华为版下载v1.400052.496077 安卓版 凹凸曼大作战官方下载-凹凸曼大作战游戏下载v0.920.0 安卓版
凹凸曼大作战官方下载-凹凸曼大作战游戏下载v0.920.0 安卓版 现代战争尖峰对决国际服下载-现代战争尖峰对决国际版下载v1.16.22 安卓版
现代战争尖峰对决国际服下载-现代战争尖峰对决国际版下载v1.16.22 安卓版 王牌战争vivo版下载手机版-王牌战争vivo版本下载v4.3 安卓版
王牌战争vivo版下载手机版-王牌战争vivo版本下载v4.3 安卓版 堡垒乱斗手游下载-堡垒乱斗免费版下载v1.1 安卓最新版
堡垒乱斗手游下载-堡垒乱斗免费版下载v1.1 安卓最新版
魔兽3地图:哲殿
 游戏地图 / 184.89MB / 2011-3-27 / WinXP, Win7, win8 / / 下载
游戏地图 / 184.89MB / 2011-3-27 / WinXP, Win7, win8 / / 下载
魔兽地图:神之墓地2.8c修改版
 游戏地图 / 865.28MB / 2012-11-7 / WinAll, WinXP, Win7, win8 / / 下载
游戏地图 / 865.28MB / 2012-11-7 / WinAll, WinXP, Win7, win8 / / 下载
魔兽地图:布诺尔世界的传说
 游戏地图 / 635.62MB / 2014-9-24 / WinAll, WinXP, Win7, win8 / / 下载
游戏地图 / 635.62MB / 2014-9-24 / WinAll, WinXP, Win7, win8 / / 下载
我的世界搞点事跑酷地图
 游戏地图 / 583.8MB / 2019-10-5 / WinAll, WinXP, Win7, win8 / / 下载
游戏地图 / 583.8MB / 2019-10-5 / WinAll, WinXP, Win7, win8 / / 下载
魔兽地图:乱世三国2.5.8正式版
 游戏地图 / 986.46MB / 2021-5-14 / WinAll, WinXP, Win7, win8 / / 下载
游戏地图 / 986.46MB / 2021-5-14 / WinAll, WinXP, Win7, win8 / / 下载
求生之路2生化危机1非官方地图
 游戏地图 / 946.98MB / 2023-3-26 / WinAll, WinXP, Win7, win8 / / 下载
游戏地图 / 946.98MB / 2023-3-26 / WinAll, WinXP, Win7, win8 / / 下载
妖精尾巴公会战2.1.32[T]
 游戏地图 / 132.38MB / 2017-5-29 / WinAll, WinXP, Win7, win8 / / 下载
游戏地图 / 132.38MB / 2017-5-29 / WinAll, WinXP, Win7, win8 / / 下载
自由之城1.4【无CD无限蓝P闪】
 游戏地图 / 760.84MB / 2018-10-12 / WinAll, WinXP, Win7, win8 / / 下载
游戏地图 / 760.84MB / 2018-10-12 / WinAll, WinXP, Win7, win8 / / 下载
幸运战争1.27
 游戏地图 / 200.67MB / 2022-10-7 / WinAll, WinXP, Win7, win8 / / 下载
游戏地图 / 200.67MB / 2022-10-7 / WinAll, WinXP, Win7, win8 / / 下载
逃脱大师脑洞地带第二季2.0.14
 游戏地图 / 819.8MB / 2021-10-25 / WinAll, WinXP, Win7, win8 / / 下载
游戏地图 / 819.8MB / 2021-10-25 / WinAll, WinXP, Win7, win8 / / 下载
无极天下1.0.3正式版
 游戏地图 / 789.20MB / 2019-10-21 / WinAll, WinXP, Win7, win8 / / 下载
游戏地图 / 789.20MB / 2019-10-21 / WinAll, WinXP, Win7, win8 / / 下载
讨伐大魔王1.0.9【隐藏英雄密码】
 游戏地图 / 262.45MB / 2018-8-6 / WinAll, WinXP, Win7, win8 / / 下载
游戏地图 / 262.45MB / 2018-8-6 / WinAll, WinXP, Win7, win8 / / 下载
末世佣兵1.0C
 游戏地图 / 892.36MB / 2010-3-17 / WinAll, WinXP, Win7, win8 / / 下载
游戏地图 / 892.36MB / 2010-3-17 / WinAll, WinXP, Win7, win8 / / 下载